Can smart grids be protected from PNT cyberattacks?

By Nino De Falcis, Senior Director of Business Development, ADVA
Today’s critical network infrastructure is heavily reliant on positioning, navigation and timing (PNT) services. Power grids, financial markets, transportation, data centers, communications — all have become more complex and interconnected, while the threats to the PNT on which they depend have grown in frequency and sophistication. PNT systems are so vulnerable to the activities of cybercriminals that attacks may soon become global in scale and significance, with potential costs of billions of dollars.
Utilities are a key example of infrastructure at risk. In the past, power networks were passive systems with everything simple and centralized, and with energy flowing in one direction only as AC power was provided to consumers. However, the growth in renewables and distributed energy resources has spurred diversification of the market, and a new paradigm of bidirectional AD and DC energy production and distribution has emerged: the smart grid.
Timing Challenges
Today, many smaller producers are generating power from multiple sources. The power grid has become a decentralized system and the flow of energy is now bidirectional. Energy from solar panels (microgrids), for example, can be generated by private individuals and either stored or fed back into the grid. Electric vehicles (EVs) are also becoming more common, and like all other nodes across the smart grid, charging points require precise timestamping of the massive amount of data they generate to balance power demand and supply.
Precise timing is also key to rerouting power flows away from transmission outages, to locating power line faults, and for synchronizing distributed control and protection systems. Without highly accurate timing and synchronization, power grids are vulnerable to partial outages and even complete blackouts.
That is why accuracy requirements of data timestamping are tighter than ever. In fact, they are shifting from legacy Network Timing Protocol (NTP) timestamping, which has millisecond accuracy needs, to Precision Timing Protocol (PTP) timestamping, requiring sub-microsecond accuracy. The syncrophaser now demands accuracy better than 1 microsecond.
For fault location, we’re now at 100 nanoseconds. The micro-phasor measurement unit (PMU) is at less than 1 microsecond and substation LAN communication protocols have to be time-stamped at as low as 100 microseconds for GOOSE IEC 61850 and at 1 microsecond for IEC 61850 sample values. This is a big change from just five years ago when accuracy in all these categories was firmly in the millisecond range, and it’s a high bar that needs to be maintained by next-generation redundant systems, should GPS or ground-based timing become compromised.
New Standards
Guidelines for making PNT infrastructure fully redundant are being pushed by governments across the world. In the United States, regulations are being driven by Executive Order 13905 with the Department of Homeland Security (DHS) providing a framework for how assured PNT (aPNT) should operate. It states that PNT infrastructure must perform three core functions: prevent, respond and recover. Infrastructure must have the ability to prevent atypical PNT errors and corruption of PNT sources. If prevention fails, networks must be able to respond to detected errors or anomalies and then recover from those errors.
The DHS framework outlines four resiliency levels. Level 1 has only one source providing PNT, while level 4 is a next-generation system leveraging multiple sources to derive and distribute PNT data. At Level 4, systems need to be self-survivable. This means they must function for long periods in the absence of a GPS timing source, or when ground-based timing sources have been otherwise compromised. There is even an IEEE P1952 resilient PNT standard in progress that will use this DHS framework.
Rising Threats
There are two categories of threat to PNT: external and internal. External threats include jamming (equipment that can block GPS is available off the shelf for as little as $20) and spoofing, which is the act of transmitting false GPS signals that trick receivers into calculating an erroneous position. Sophisticated cyberattacks can be in the form of either of these and spoofing (especially synchronous) is the most complex to detect.
The two main internal PNT threats come from attacks on NTP and PTP network timing as well as active GPS receivers connected to the network.
Legacy power grids have traditionally used NTP to distribute timing to substations, including IRIG, and this has already shown itself to be vulnerable to attack because it can be hacked by a process called NTP amplification.
Today, power grids are increasingly migrating to PTP because it provides the sub-microsecond accuracy needed for modern applications. PTP also has not yet been hacked, but that does not mean it soon will not be. If an attack did occur on ill-prepared critical infrastructure, the results could be catastrophic.
Secure Smart Grid Timing Components
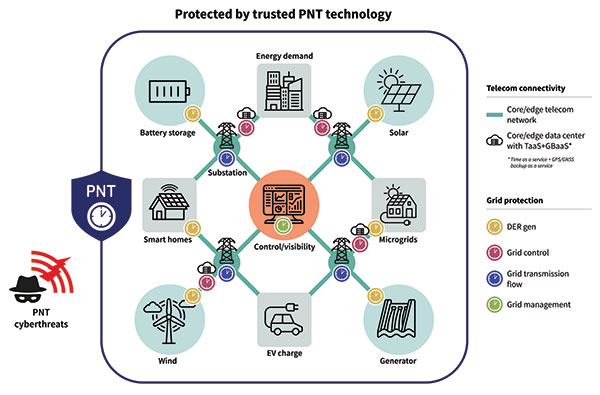
There are two components in the smart grid: telecom connectivity to transport data, and grid protection that has different level generation grid control, transmission and management. On the telecom side, there is the edge telecom network and sometimes there are data centers. There are either core or edge data centers and these are also equipped with very good timing. A key concept in the data center is time as a service and GPS backup as a service when GPS goes down. The smart grid can also leverage this service as it gives even more robust protection and security against threats to PNT. See Diagram 1.
A Resilient and Assured PNT Solution
As with other aspects of cybersecurity strategy, smart grids must employ a zero-trust framework of PNT sources. This approach never assumes that any one PNT source can be trusted. Instead, it uses a multi-source approach, verifying sources and comparing them to each other in real time to get the most accurate timing possible.
To prevent and mitigate interruptions to GPS, smart grid operators should deploy a resilient and assured PNT solution. This means it’s based around three integrated technologies: multi-layer detection, multi-source backup and multi-level fault-tolerant mitigation.
Multi-layer detection is performed through timing devices – either single or redundant – that have jamming and spoofing detection and monitoring capabilities. GNSS devices are also capable of comparing sources such as network PTP timing and they can be equipped with standalone, GNSS-backup clocks that leverage rubidium or cesium oscillators to obtain the most reliable timing information from other timing sources in the network.
Multi-source backup comes in the form of a cesium or rubidium oscillator that can provide extended holdover. Backup can be further bolstered with other sources such as eLORAN, NIST and LEO.
A neural network management system is an intelligent platform that ties everything together, from self-actionable recovery and assurance software to alerting users of issues in the network-wide timing infrastructure. It provides visibility and control of all aspects of prevention, mitigation and backup. The management system gives detailed operational data on the smart grid, showing the locations of the faults, the types of faults, and how PTP backup assurance is performing. Through capabilities powered by artificial intelligence and machine learning, the management and control system provides the end-to-end control, visibility, and trusted, assured PNT. It has all the intelligence to reveal threats and also take action against them, quickly recovering the network’s timing distribution capability, while keeping the network timing self-survivable. See Diagram 2.
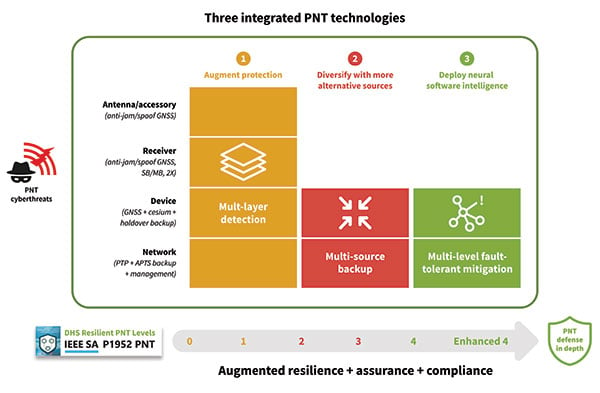
Diagram 2. Defending against PNT cyberthreats requires integrating multiple PNT technologies. (Image: ADVA)
Mitigating Cyberattacks with a Defense-in-Depth Approach
So, let us imagine there is a major attack on a smart grid. A jamming device has been used to block GPS reception on an edge grandmaster being used at a substation, while at the core of the network an ePRTC’s ability to receive GNSS signals has also been compromised. GPS is no longer viable as a source for timing in the smart grid.
The intelligent software monitoring and management system is the first line of defense, detecting and alerting operators to the two or more attacks on GPS: one at the core of the network and one at the substation. The network timing capability of the whole smart grid has been compromised.
Upstream from the substation, the core enhanced PRTC (ePRTC) has become an unreliable source of timing. However, it is equipped with a cesium clock that steps in to propagate trusted PNT backup into the substation and throughout the rest of the network. The cesium clock has no antenna, no RH signal, and is a stratum 1 clock that can propagate highly accurate timing (accurate to 1 microsecond over four months) throughout the network. It has now become the trusted source of timing until GPS can be re-established.
Time for Multi-Source Protection
The most crucial element of PNT is timing. Without timing there is no positioning or navigation — it is the enabler of both — and so the distribution of accurate timing must be our top concern when we build systems.
For smart grids and all other critical infrastructure dependent on PNT to function, the cornerstone for secure and self-survivable timing networks is the concept of zero-trust. A multi-source approach to building timing networks will allow operators of critical infrastructure to leverage a combination of intelligent management software and timing devices equipped with adequate PTP holdover to respond to all threats to PNT.
To see a real-world example of this approach in action, check out the DOE DarkNet program.


















Follow Us