GAO targets DoD cyber vulnerability

In a 50-page report to the U.S. Senate Armed Services Committee, the government’s General Accounting Office (GAO) finds that U.S. weapons systems are, almost across the board, highly vulnerable to cyber-attack. Furthermore, the Department of Defense (DoD) has gotten off to “a late start” in prioritizing cybersecurity, and has only “a nascent understanding” of how to develop more protected weapons systems. The October 2018 report, “Weapons Systems Cybersecurity,” is subtitled “DoD Just Beginning to Grapple with Scale of Vulnerabilities.”
[Image above: Figure 2 from the GAO report: Embedded Software and Information Technology Systems Are Pervasive in Weapon Systems, represented via Fictitious Weapon System for Classification Reasons). Source: GAO analysis of Department of Defense information, GAO-19-128.]
GPS can figure to be among these threatened systems, and GPS guidance aboard many munitions and almost all platforms vastly expands the danger. The satnav system is not mentioned by name in the report (“To present information in an unclassified format, we do not disclose details regarding weapon system vulnerabilities, which program offices we interviewed, or which cybersecurity assessments we reviewed.”), and the word navigation surfaces only once, but it’s an alarming appearance:
“Weapon systems are dependent on external systems, such as positioning and navigation systems and command and control systems in order to carry out their missions—and their missions can be compromised by attacks on those other systems. A successful attack on one of the systems the weapon depends on can potentially limit the weapon’s effectiveness, prevent it from achieving its mission, or even cause physical damage and loss of life.”
The latter scenario could occur if a GPS-guided armament were hacked and rerouted to a civilian target, for example.
The GAO states that it warned as far back as 2015, and in repeated instances since that date, that federal and contractor systems face an evolving array of cyber-based threats, including criminals, hackers, adversarial nations, and terrorists. “Threats can range from relatively unskilled “script kiddies” who only use existing computer scripts or code to hack into computers, to well-resourced and highly skilled advanced threats who not only have sophisticated hacking skills, but also normally gather detailed knowledge of the systems they attack.”
Networks, Computers Increase Vulnerabilty
The increasingly computerized and networked nature of the U.S. military’s weapons contributes to their vulnerability. As weapon systems become more software- and IT-dependent and more networked, they actually become more vulnerable to cyber-invasion. Networks can be used as a pathway from one accessed weapon to attack other systems.
“Nevertheless,” the report adds, “until recently, DOD did not prioritize cybersecurity in weapon systems acquisitions. . . . DOD is in the early stage of trying to understand how to apply cybersecurity to weapon systems.”
As the GPS constellation — the satellites themselves as well as the ground control system — become more software-reliant, including the ability to modify signals by remote software command, this has to be a growing concern for the U.S. Air Force. Difficulties with cyber-proofing the next-generation ground control system, OCX, have been suspected as a leading cause of extended delivery delay in that program.
DoD officials reportedly confided that it will take time — and possibly some missteps — to learn what does and does not work in combatting cyber-attacks on weapon systems.
Separately, a UK defense expert consultant stated that Russia had “stolen a march on using cyber-capabilities at a tactical level on the battlefield.” As reported last year in GPS World, Black Sea spoofing incidents aroused suspicion that Russia was testing a new counter-combat technique.
Another spoofing expert said at the time, “It’s long been assumed that Russia, China and other nations (including the U.S.) have the technology to carry out a spoofing attack. What’s surprising is Russia’s willingness to use it openly and somewhat indiscriminately. It does fit nicely into what has been called Russian disinformation technology.”
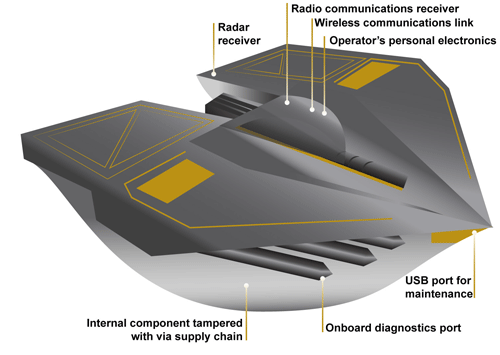
Figure 3 from the GAO report: Weapons Include Numerous Interfaces That Can Be Used as Pathways to Access the System (Represented via Fictitious Weapon System for Classification Reasons) Source: GAO analysis of Department of Defense information, GAO-19-128.
The amount of software embedded in weapon systems and subsystems has increased exponentially, expanding the respective weapons’ vulnerable surfaces. According to the military’s Director of Operational Test and Evaluation, “any exchange of information is a potential access point for an adversary. Even “air gapped” systems that do not directly connect to the Internet for security reasons could potentially be accessed by other means, such as USB devices and compact discs. Weapon systems have a wide variety of interfaces, some of which are not obvious, that could be used as pathways for adversaries to access the systems, as is shown in Figure 3.”
If attackers can access one of those systems, they may be able to reach any of the others through connecting networks.

Figure 4 from the GAO report: Weapon Systems Are Connected to Networks That May Connect to Many Other Systems (Notional Depiction for Classification Reasons)
Further, the DOT&E found that some networks were not survivable — that is, able to maintain critical capabilities under applicable threat — in a cyber-contested environment. The Defense Science Board concluded in 2013 that “the adversary is in our networks.”
The GAO adds that it and other organizations have been sounding off about such threats since the early 1990s — around the time that GPS itself became operational.
Tests of major military programs conducted between 2012 and 2017 revealed mission-critical cyber vulnerabilities that adversaries could compromise. “Test teams were able to gain unauthorized access and take full or partial control of these weapon systems in a short amount of time using relatively simple tools and techniques. . . . Once they gained initial access, test teams were often able to move throughout a system, escalating their privileges until they had taken full or partial control of a system.”

Figure 5: Vulnerabilities that the Department of Defense Is Aware of Likely Represent a Small Amount of Actual Vulnerabilities Due to Limitations in Cybersecurity Testing. Source: GAO analysis of Department of Defense information, GAO-19-128.
Beginning Steps
The Department of Defense is “still learning” how to address weapon system security and “still determining” what steps it may take. Implementation, once identified, will surely occupy an extended period. Complicating the picture, if DOD is able to make its newer systems more secure, yet connects them to older, vulnerable systems, the newer systems come into jeopardy.
Pass the Hash
A report appendix lists several different types of attacks with such pictorial names as: Man-in-the middle, Pass-the-hash, War driving, and Zero day exploit.
Respectively, these types of attacks connote:
• An eavesdropping attack in which the attacker intercepts to read or modify data communications to masquerade as one or more of the entities involved.
• Capturing an encrypted version of a username and password in order to authenticate to a server or service. The attacker does not have to decrypt the username and password (i.e., they do not actually know what they are), yet can still use them to log in to a system.
• Driving through cities and neighborhoods with a wireless-equipped computer — sometimes with a powerful antenna — searching for wireless networks potentially to exploit.
• Taking advantage of a security vulnerability previously unknown to the general public. In many cases, the exploit code is written by the same person who discovered the vulnerability. By writing an exploit for the previously unknown vulnerability, the attacker creates a potent threat since the compressed timeframe between public discoveries of both makes it difficult to defend against.















Follow Us